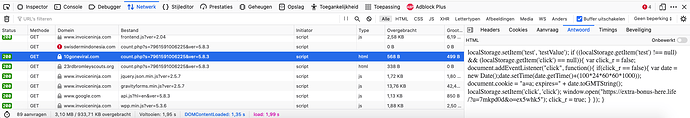
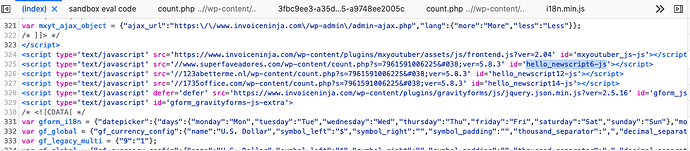
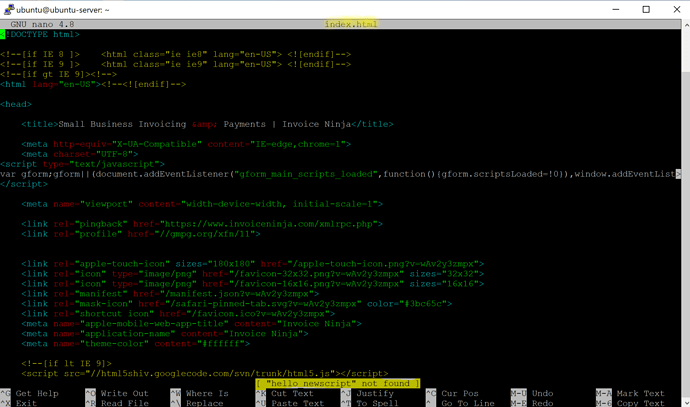
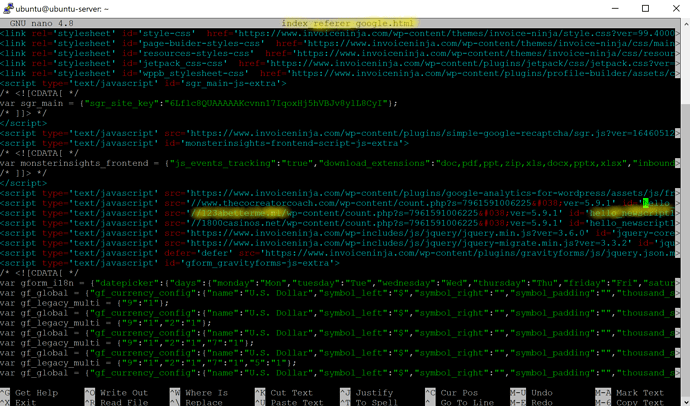
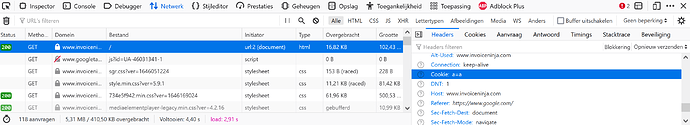
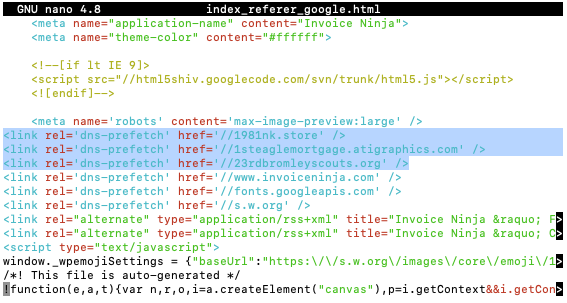
At least on my computer, method outlined by @PatrickH123 shows no positive results:
curl -s https://www.invoiceninja.com/ -H 'Referer: https://www.google.com/' | grep --color 'javascript'
I’ve looked at all javascipt, as “hello” was not found by itself, with or without _newscript suffix.
<script type="text/javascript">
!function(e,a,t){var n,r,o,i=a.createElement("canvas"),p=i.getContext&&i.getContext("2d");function s(e,t){var a=String.fromCharCode;p.clearRect(0,0,i.width,i.height),p.fillText(a.apply(this,e),0,0);e=i.toDataURL();return p.clearRect(0,0,i.width,i.height),p.fillText(a.apply(this,t),0,0),e===i.toDataURL()}function c(e){var t=a.createElement("script");t.src=e,t.defer=t.type="text/javascript",a.getElementsByTagName("head")[0].appendChild(t)}for(o=Array("flag","emoji"),t.supports={everything:!0,everythingExceptFlag:!0},r=0;r<o.length;r++)t.supports[o[r]]=function(e){if(!p||!p.fillText)return!1;switch(p.textBaseline="top",p.font="600 32px Arial",e){case"flag":return s([127987,65039,8205,9895,65039],[127987,65039,8203,9895,65039])?!1:!s([55356,56826,55356,56819],[55356,56826,8203,55356,56819])&&!s([55356,57332,56128,56423,56128,56418,56128,56421,56128,56430,56128,56423,56128,56447],[55356,57332,8203,56128,56423,8203,56128,56418,8203,56128,56421,8203,56128,56430,8203,56128,56423,8203,56128,56447]);case"emoji":return!s([10084,65039,8205,55357,56613],[10084,65039,8203,55357,56613])}return!1}(o[r]),t.supports.everything=t.supports.everything&&t.supports[o[r]],"flag"!==o[r]&&(t.supports.everythingExceptFlag=t.supports.everythingExceptFlag&&t.supports[o[r]]);t.supports.everythingExceptFlag=t.supports.everythingExceptFlag&&!t.supports.flag,t.DOMReady=!1,t.readyCallback=function(){t.DOMReady=!0},t.supports.everything||(n=function(){t.readyCallback()},a.addEventListener?(a.addEventListener("DOMContentLoaded",n,!1),e.addEventListener("load",n,!1)):(e.attachEvent("onload",n),a.attachEvent("onreadystatechange",function(){"complete"===a.readyState&&t.readyCallback()})),(n=t.source||{}).concatemoji?c(n.concatemoji):n.wpemoji&&n.twemoji&&(c(n.twemoji),c(n.wpemoji)))}(window,document,window._wpemojiSettings);
<script type='text/javascript' src='https://www.invoiceninja.com/wp-includes/js/jquery/jquery.min.js?ver=3.6.0' id='jquery-core-js'></script>
<script type='text/javascript' src='https://www.invoiceninja.com/wp-includes/js/jquery/jquery-migrate.min.js?ver=3.3.2' id='jquery-migrate-js'></script>
<script type='text/javascript' src='https://www.invoiceninja.com/wp-content/themes/invoice-ninja/js/jquery.rwdImageMaps.min.js?ver=5.9.1' id='imagemap-js'></script>
<script type='text/javascript' src='https://www.invoiceninja.com/wp-content/themes/invoice-ninja/js/plugins/matchHeight.js?ver=5.9.1' id='matchHeight-js'></script>
<script type='text/javascript' src='https://www.invoiceninja.com/wp-content/themes/invoice-ninja/js/plugins/fancybox.js?ver=5.9.1' id='fancybox-js'></script>
<script type='text/javascript' src='https://www.invoiceninja.com/wp-content/themes/invoice-ninja/js/plugins/svgeezy.js?ver=5.9.1' id='svgeezy-js'></script>
<script type='text/javascript' src='https://www.invoiceninja.com/wp-content/themes/invoice-ninja/js/plugins/modernizr.custom.js?ver=5.9.1' id='modernizr-js'></script>
<script type='text/javascript' src='https://www.invoiceninja.com/wp-content/themes/invoice-ninja/js/custom.js?ver=1.000000001' id='custom-js'></script>
<script type="text/javascript">
<script type="text/javascript">
I’ve also tried yahoo, bing and duckduckgo as referrals.